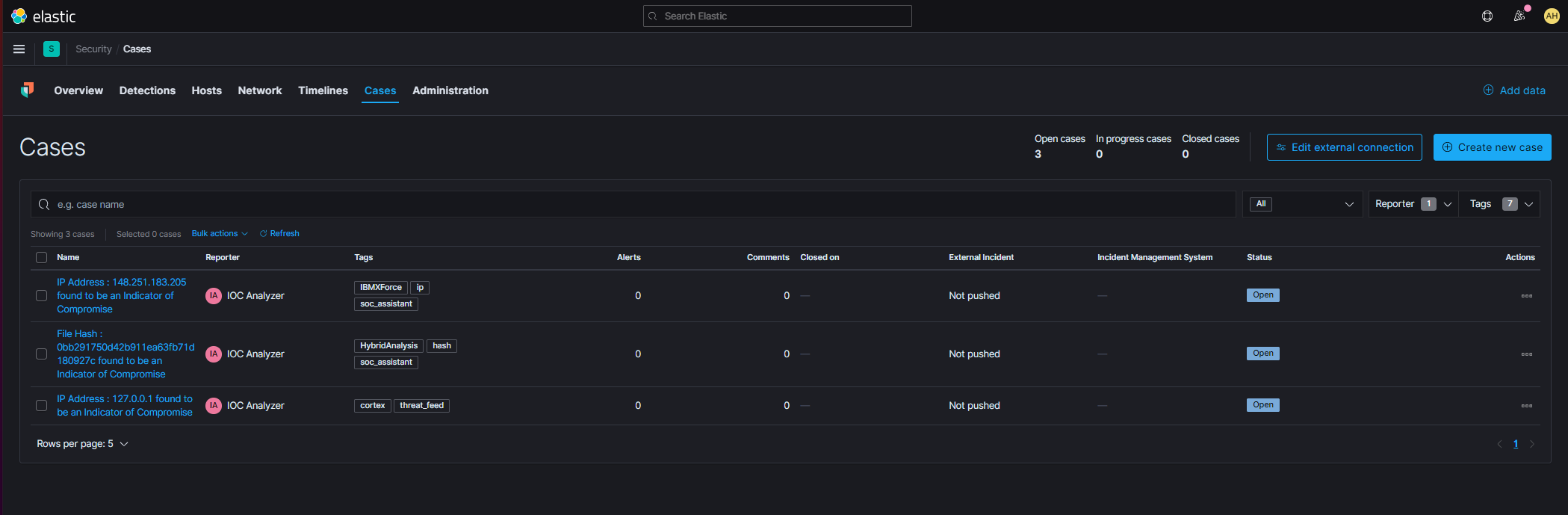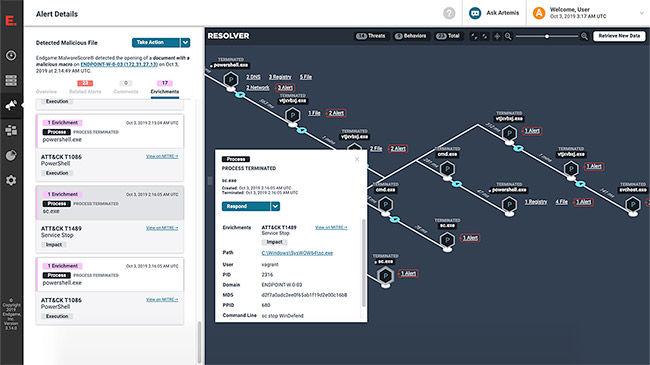
Elastic blends SIEM and endpoint security into a single solution for real-time threat response - Help Net Security

Threat Hunting with Elastic Stack: Solve complex security challenges with integrated prevention, detection, and response: 9781801073783: Computer Science Books @ Amazon.com

Chris Townsend: Elastic Pledges Threat Intelligence Input in Joint Cyber Defense Collaborative - ExecutiveBiz
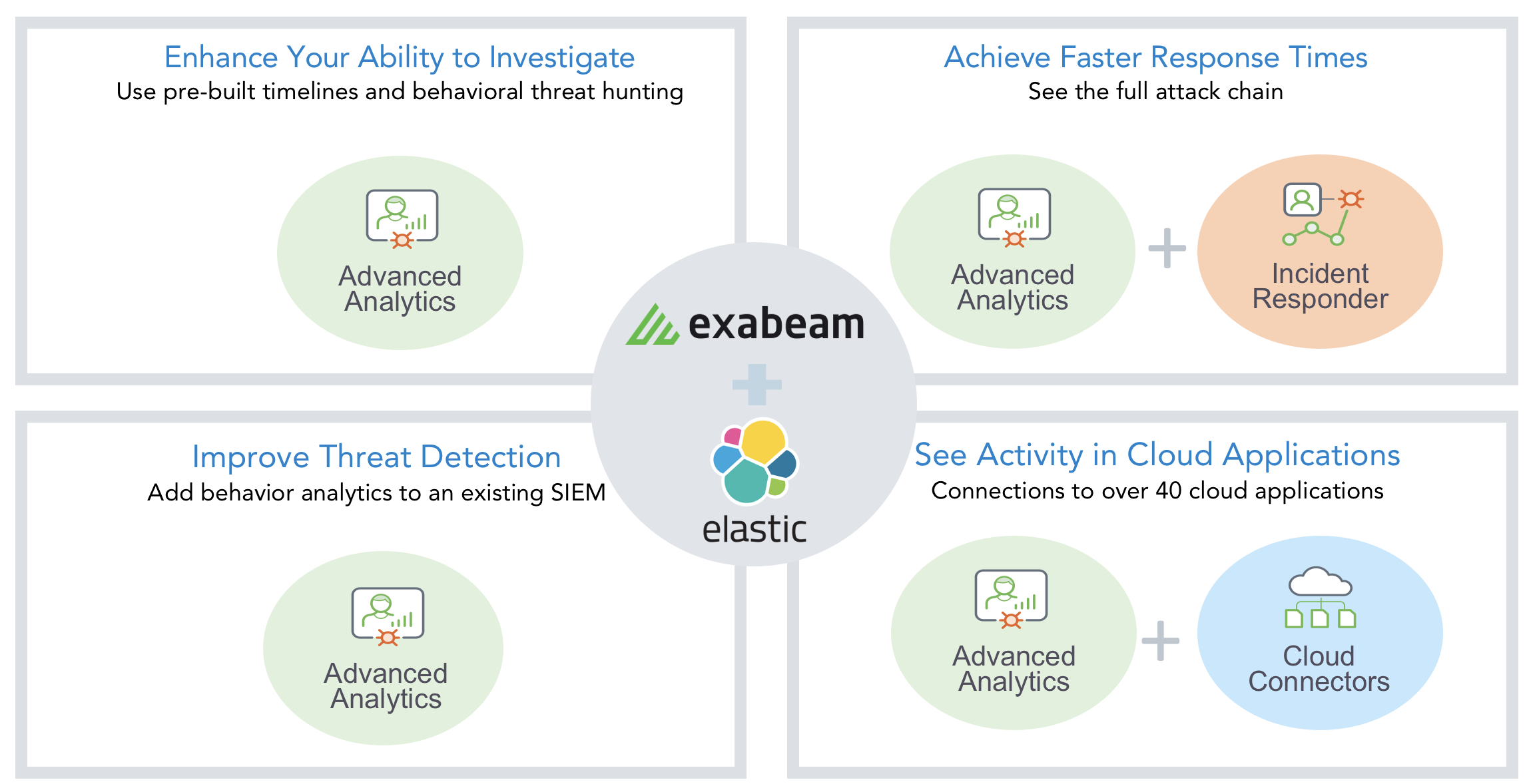

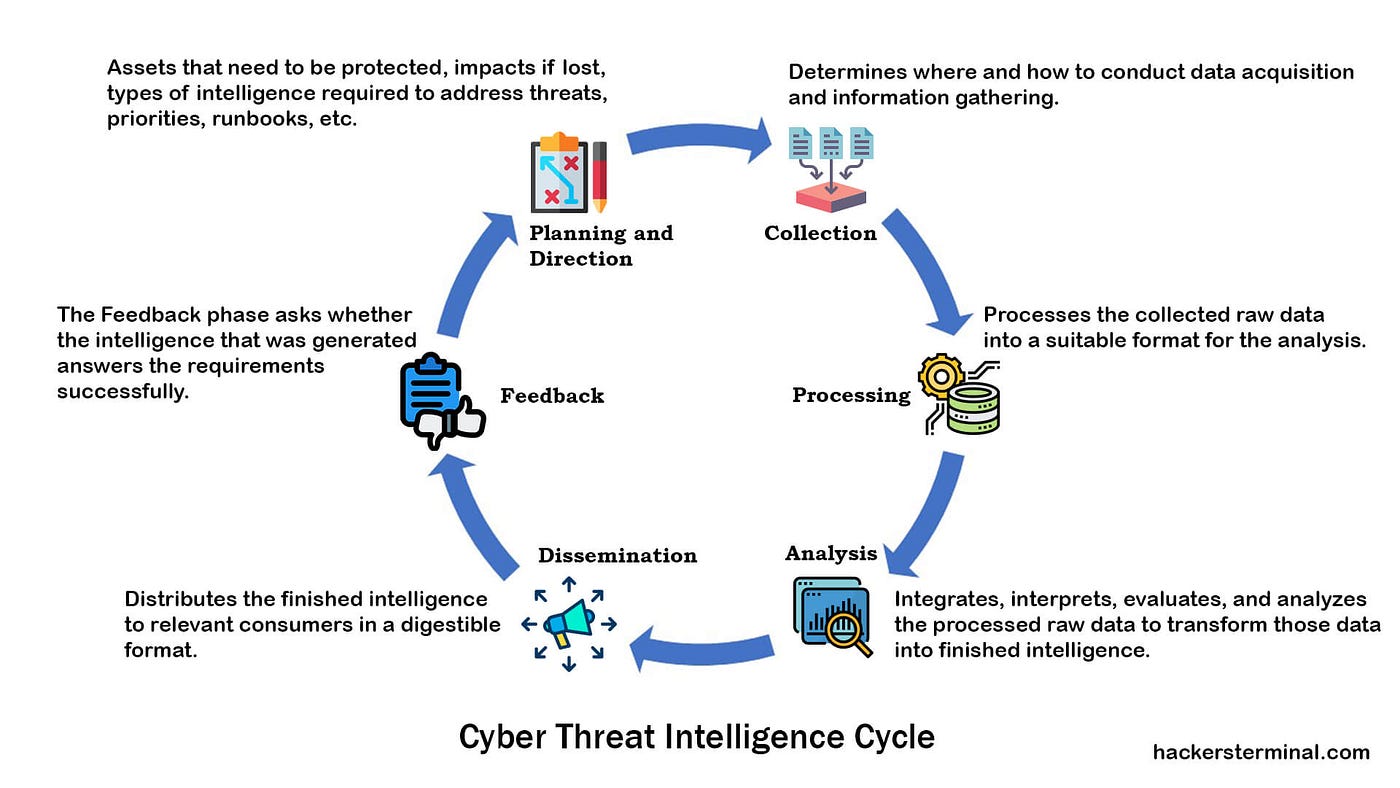
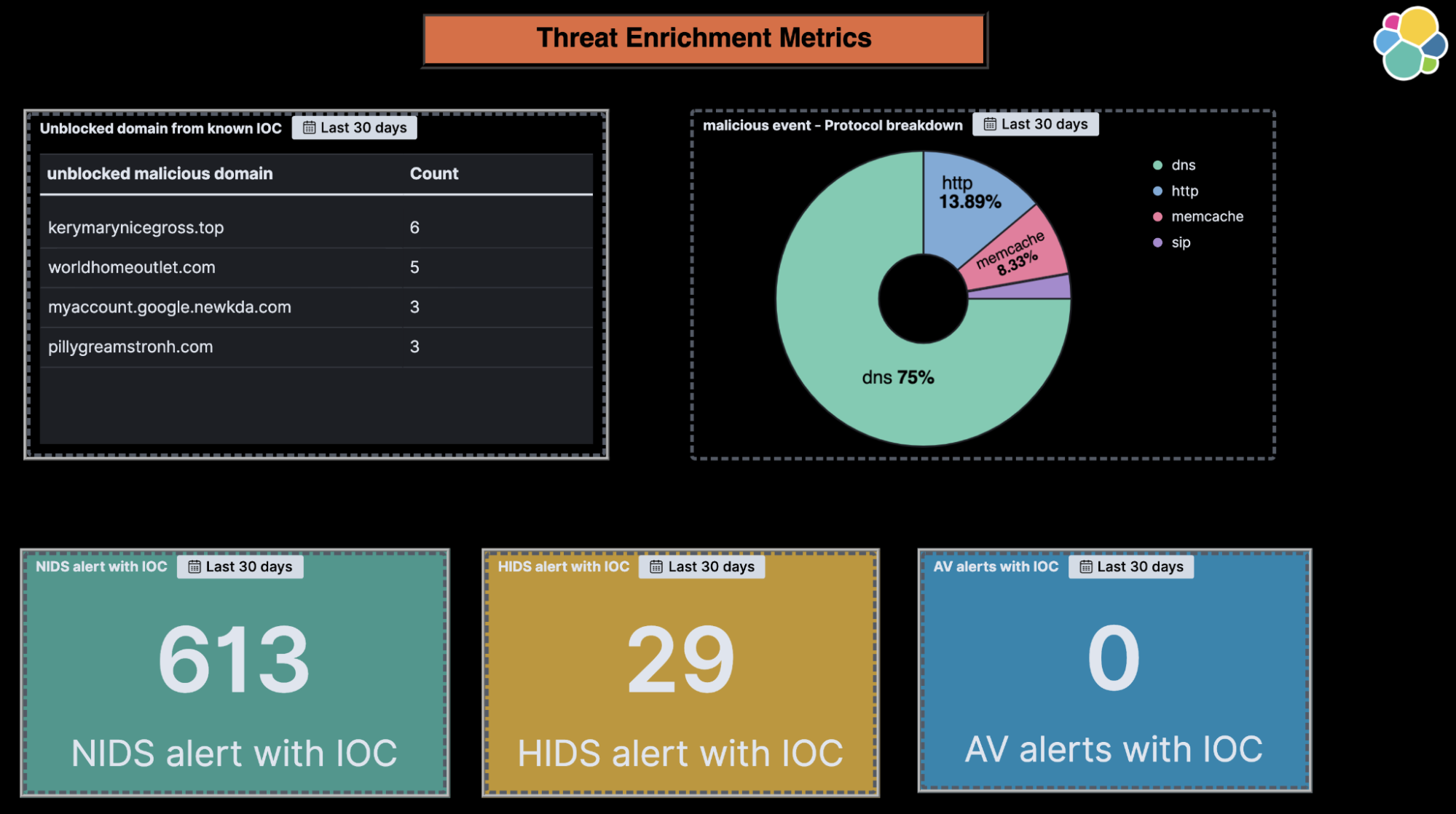


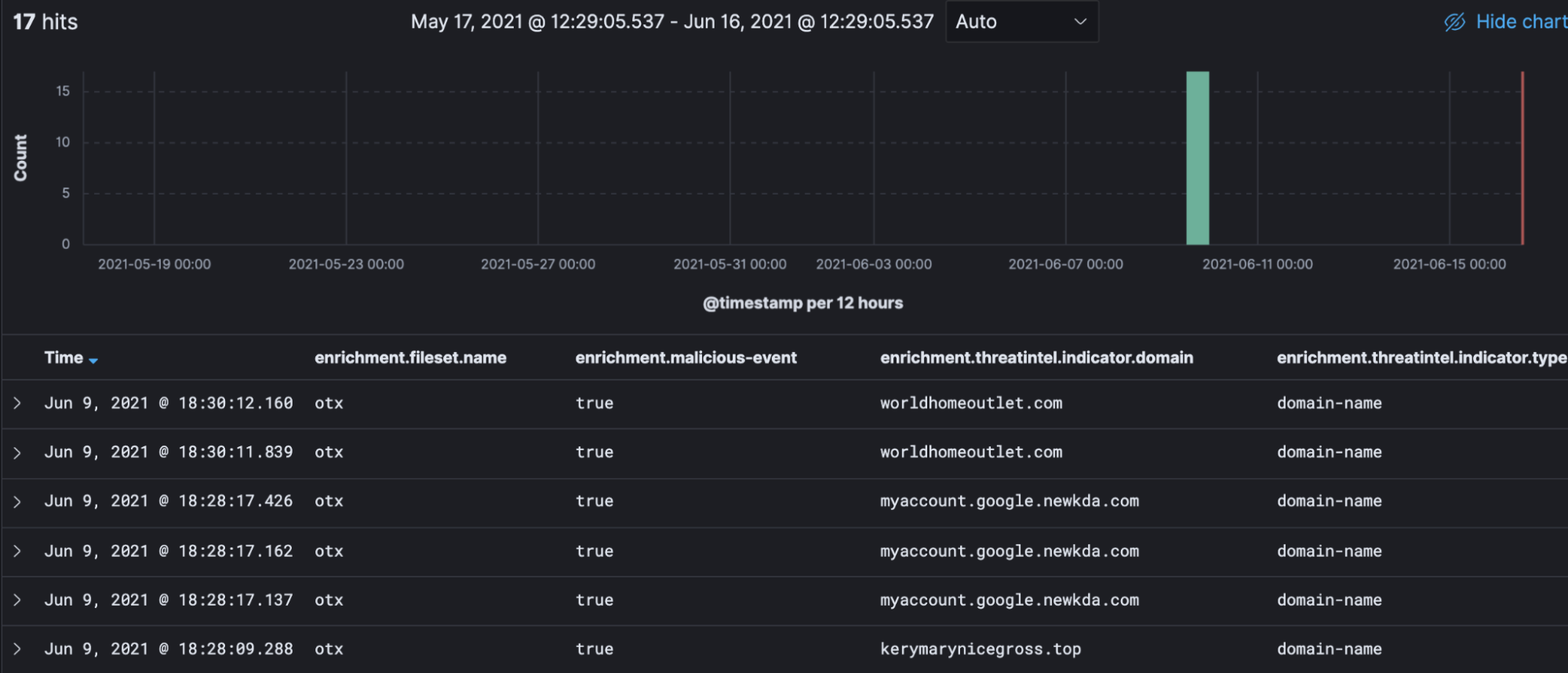



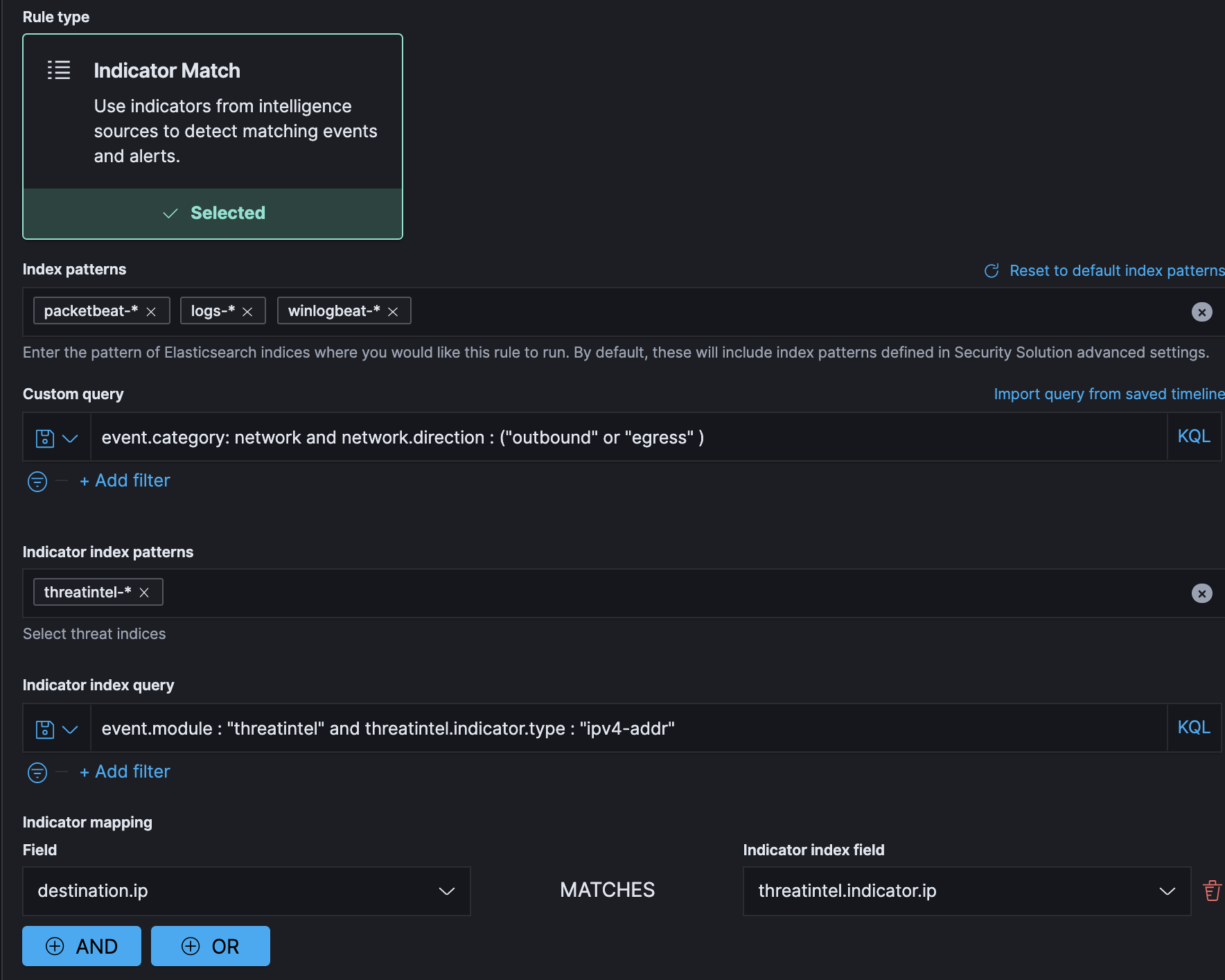


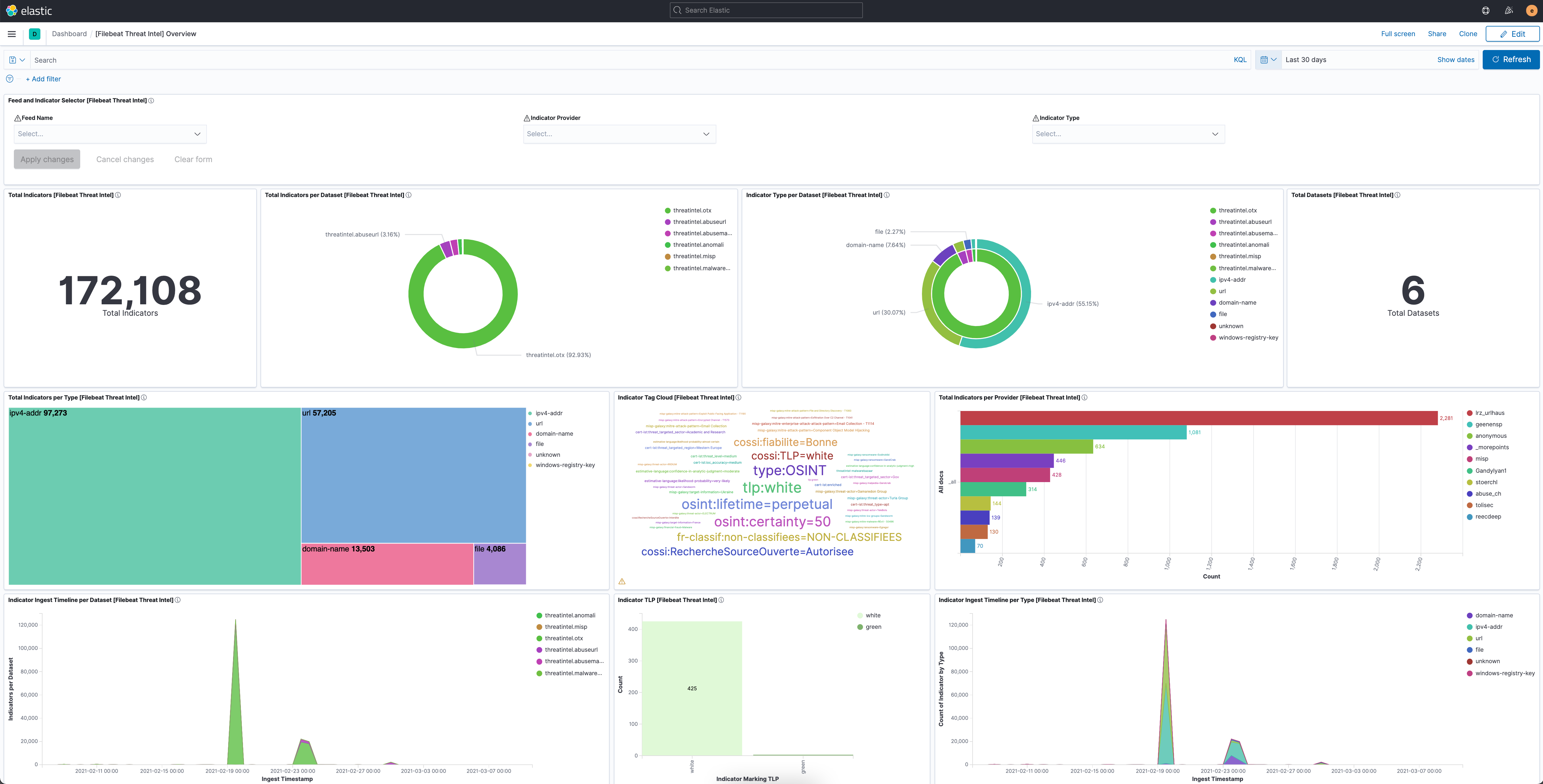

![Threat Intel module | Filebeat Reference [8.11] | Elastic Threat Intel module | Filebeat Reference [8.11] | Elastic](https://www.elastic.co/guide/en/beats/filebeat/current/images/filebeat-threatintel-abuse-url.png)
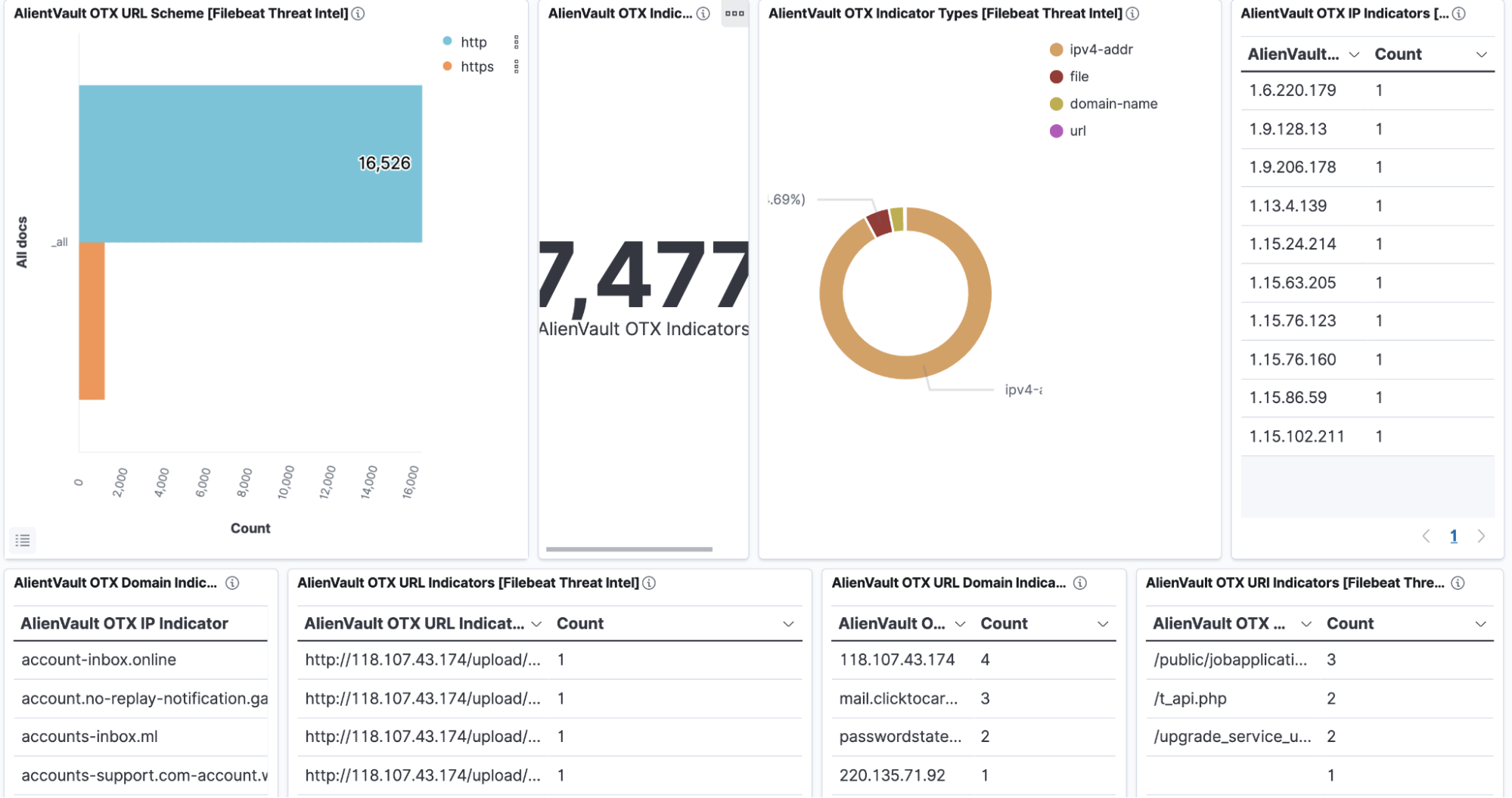

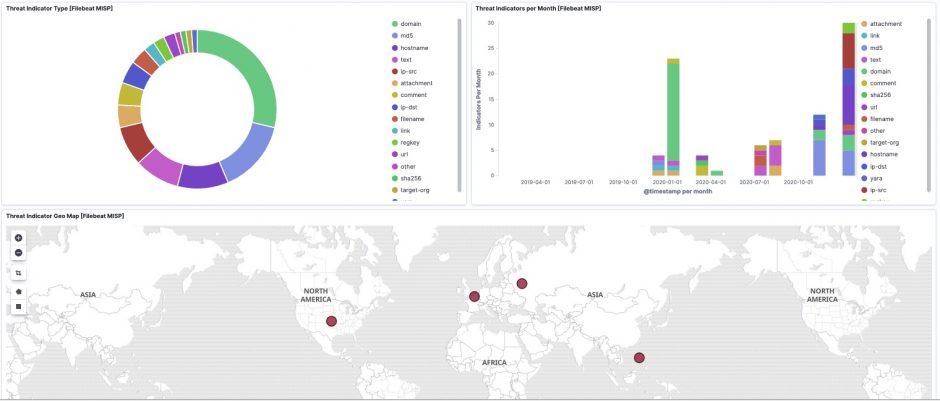

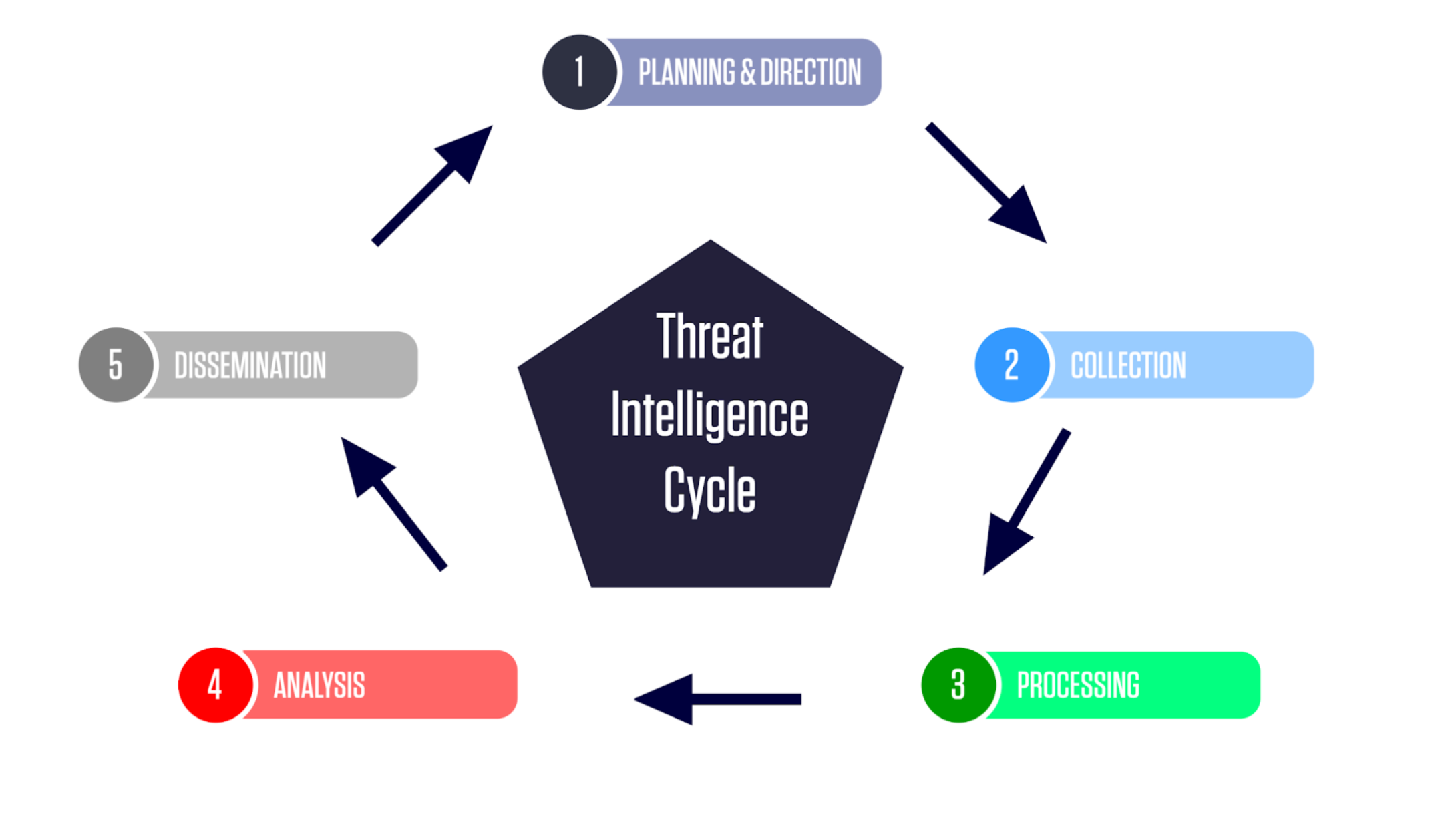
.png?width=1160&height=956&name=Untitled%20(6).png)